Difference between revisions of "Firewall Rules"
m |
m (small typing errors) |
||
| (6 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | {{versioninfo|810Status=relevant|810UpdatedDate=21 Aug 2011|810UpdatedBy=[[User:Foxi352|Foxi352]]|1004Status=relevant|1004UpdatedDate=21 Aug 2011|1004UpdatedBy=[[User:Foxi352|Foxi352]] | |
| − | {{versioninfo|810Status=relevant|810UpdatedDate=21 Aug 2011|810UpdatedBy=Foxi352}} | + | |1204Status=relevant(read downto setion from 1204)|1204UpdatedDate=19 Jul 2014|1204UpdatedBy=[[User:Alblasco1702|Alblasco1702]]}} |
[[Category:Admin Website]] | [[Category:Admin Website]] | ||
[[Category:Networking]] | [[Category:Networking]] | ||
| − | |||
| − | |||
[[Image:Firewall.jpg|thumb|200px|Firewall Rules Admin Page]] | [[Image:Firewall.jpg|thumb|200px|Firewall Rules Admin Page]] | ||
This page allows you to customize your firewall rules, even disabling the firewall. When first opened you will notice that there are several predefined rules already in place. | This page allows you to customize your firewall rules, even disabling the firewall. When first opened you will notice that there are several predefined rules already in place. | ||
| + | ==from 0810 to 10.04== | ||
==Options== | ==Options== | ||
[[Image:FirewallOptions.jpg]] | [[Image:FirewallOptions.jpg]] | ||
| Line 41: | Line 40: | ||
===Limit IP=== | ===Limit IP=== | ||
You can limit rules to specific IP addresses. | You can limit rules to specific IP addresses. | ||
| + | |||
| + | It looks like you can add the mask to specify ranges: 134.78.0.0/16 | ||
| + | |||
| + | ==from 1204== | ||
| + | |||
| + | ===Select Firewall=== | ||
| + | select the firewall version (ipv4/ipv6). | ||
| + | |||
| + | ===Advanced Firewall Settings=== | ||
| + | if selected you see the rules defined on all default or manual defined chains. | ||
| + | |||
| + | ===Show all unprocessed rules=== | ||
| + | show all rules even if they are not set to the firewall. | ||
| + | |||
| + | ===Block TOP20 known attackers=== | ||
| + | Greps a list every hour and set those on the chain Blocklist, | ||
| + | a list with the TOP 20 known attackers are blocked to the system. | ||
| + | |||
| + | ===Options=== | ||
| + | [[Image:[[File:FirewallOptionsNew.jpg]] | ||
| + | |||
| + | ===Input Interface=== | ||
| + | optional. | ||
| + | setting if you chose input or forward. | ||
| + | |||
| + | ===Output Interface=== | ||
| + | optional. | ||
| + | setting if you choose output or forward | ||
| + | |||
| + | ===Rule matching=== | ||
| + | optional | ||
| + | |||
| + | ===Protocol=== | ||
| + | Here is where you can choose the protocol involved with this rule, or define any protocol by choosing 'IP': | ||
| + | * [http://en.wikipedia.org/wiki/Transmission_Control_Protocol TCP] | ||
| + | * [http://en.wikipedia.org/wiki/User_Datagram_Protocol UDP] | ||
| + | * [http://en.wikipedia.org/wiki/Transmission_Control_Protocol TCP] & [http://en.wikipedia.org/wiki/User_Datagram_Protocol UDP] | ||
| + | * [http://en.wikipedia.org/wiki/List_of_IP_protocol_numbers IP] | ||
| + | |||
| + | ===IP version=== | ||
| + | Here you can choose if you want the rule to be active for IPv4, IPv6. | ||
| + | |||
| + | ===Source Ports=== | ||
| + | optional. | ||
| + | Choose the Ports to be used in the rule. If you chose 'IP' in the Protocol section then you can define your IP protocol (NOT PORT !!!) number here. | ||
| + | This is the port from the system where the requests are coming from so not your core!!! | ||
| + | |||
| + | ===Destination Port=== | ||
| + | Destination port on the core. | ||
| + | If you chose Port Forward (NAT) then you set 80:80 before the : you set the destination port on the core and after the : you set the port to de destination system | ||
| + | |||
| + | ===Destination IP=== | ||
| + | IP Address of the computer being forwarded to. | ||
| + | |||
| + | ===Rule Type=== | ||
| + | There are four types of rules available by default: | ||
| + | * Input | ||
| + | * forward | ||
| + | * Port Forward (NAT) | ||
| + | * output | ||
| + | |||
| + | if you add chains then they are listed here too. | ||
| + | |||
| + | the second option is with NAT to set wich type, | ||
| + | for Portforward you need prerouting option. | ||
| + | '''ToDo''' | ||
| + | on not Advanced Firewall settings mode set it automaticly to make it easyer. | ||
| + | |||
| + | ===Limit IP=== | ||
| + | You can limit rules to specific IP addresses. | ||
| + | you can add the mask to specify ranges: 134.78.0.0/16 | ||
| + | |||
| + | ===Description=== | ||
| + | optional | ||
| + | Administrative setting for you as user/network maintainer to see why this rule exists. | ||
Latest revision as of 12:02, 23 August 2015
| Version | Status | Date Updated | Updated By |
|---|---|---|---|
| 710 | Unknown | N/A | N/A |
| 810 | relevant | 21 Aug 2011 | Foxi352 |
| 1004 | relevant | 21 Aug 2011 | Foxi352 |
| 1204 | relevant(read downto setion from 1204) | 19 Jul 2014 | Alblasco1702 |
| 1404 | Unknown | N/A | N/A |
| Usage Information | |||
This page allows you to customize your firewall rules, even disabling the firewall. When first opened you will notice that there are several predefined rules already in place.
Contents
- 1 from 0810 to 10.04
- 2 Options
- 3 from 1204
- 3.1 Select Firewall
- 3.2 Advanced Firewall Settings
- 3.3 Show all unprocessed rules
- 3.4 Block TOP20 known attackers
- 3.5 Options
- 3.6 Input Interface
- 3.7 Output Interface
- 3.8 Rule matching
- 3.9 Protocol
- 3.10 IP version
- 3.11 Source Ports
- 3.12 Destination Port
- 3.13 Destination IP
- 3.14 Rule Type
- 3.15 Limit IP
- 3.16 Description
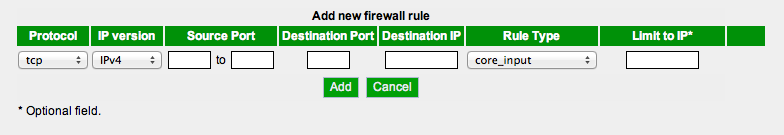
from 0810 to 10.04
Options
Protocol
Here is where you can choose the protocol involved with this rule, or define any protocol by choosing 'IP':
IP version
Here you can choose if you want the rule to be active for IPv4, IPv6 or both.
Source Ports
Choose the Ports to be used in the rule. If you chose 'IP' in the Protocol section then you can define your IP protocol (NOT PORT !!!) number here.
Destination Port
Port to forward requests to.
This option is only available if Port Forwarding is selected in the Rule Type
Destination IP
IP Address of the computer being forwarded to.
This option is only available if Port Forwarding is selected in the Rule Type
Rule Type
There are two types of rules available:
- Core Input
- Port Forward
Limit IP
You can limit rules to specific IP addresses.
It looks like you can add the mask to specify ranges: 134.78.0.0/16
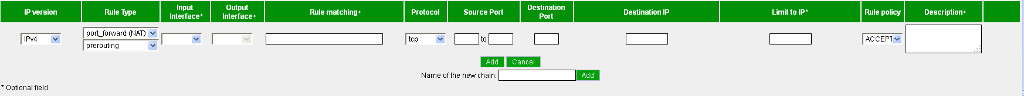
from 1204
Select Firewall
select the firewall version (ipv4/ipv6).
Advanced Firewall Settings
if selected you see the rules defined on all default or manual defined chains.
Show all unprocessed rules
show all rules even if they are not set to the firewall.
Block TOP20 known attackers
Greps a list every hour and set those on the chain Blocklist, a list with the TOP 20 known attackers are blocked to the system.
Options
Input Interface
optional. setting if you chose input or forward.
Output Interface
optional. setting if you choose output or forward
Rule matching
optional
Protocol
Here is where you can choose the protocol involved with this rule, or define any protocol by choosing 'IP':
IP version
Here you can choose if you want the rule to be active for IPv4, IPv6.
Source Ports
optional. Choose the Ports to be used in the rule. If you chose 'IP' in the Protocol section then you can define your IP protocol (NOT PORT !!!) number here. This is the port from the system where the requests are coming from so not your core!!!
Destination Port
Destination port on the core. If you chose Port Forward (NAT) then you set 80:80 before the : you set the destination port on the core and after the : you set the port to de destination system
Destination IP
IP Address of the computer being forwarded to.
Rule Type
There are four types of rules available by default:
- Input
- forward
- Port Forward (NAT)
- output
if you add chains then they are listed here too.
the second option is with NAT to set wich type, for Portforward you need prerouting option. ToDo on not Advanced Firewall settings mode set it automaticly to make it easyer.
Limit IP
You can limit rules to specific IP addresses. you can add the mask to specify ranges: 134.78.0.0/16
Description
optional Administrative setting for you as user/network maintainer to see why this rule exists.