Difference between revisions of "VPN"
(Built-in VPN) |
(More VPN description) |
||
| Line 9: | Line 9: | ||
You also need to fill in the pre-shared key and the IP range the VPN clients should use. Save the settings. | You also need to fill in the pre-shared key and the IP range the VPN clients should use. Save the settings. | ||
| − | In Wizard -> Basic Info -> Users, check the "Can connect via VPN" for every user that should be able to connect via VPN. | + | In Wizard -> Basic Info -> Users, check the "Can connect via VPN" for every user that should be able to connect via VPN. Click "Change VPN Password" for the user and enter a password for your VPN connection. |
==Connection== | ==Connection== | ||
| − | - | + | Different devices have different GUIs for setting up a VPN, so this is just a general description. To find specific description for your device, do a google search, we don't need descriptions for every possible device added to this article(Thank you!). |
| + | Enter your host name, pre-shared key and give the connection a name. The L2TP secret is not used and should be left disabled. Enter your username(case sensitive) and your VPN password. | ||
| + | |||
| + | ==Notes== | ||
| + | If you have another router or ADSL modem or something between the core and the internet, you need to check these settings: | ||
| + | You need to forward UDP ports 500(IPSEC-IKE) and 4500(IPSEC-ESP-NAT) to the core. If your device can forward protocol 50/ESP, forward this too to the core. You don't need both 4500 and the ESP protocol at the same time, find out what works for you, and disable the other one. | ||
| + | If the device has a IPSEC passthrough, it might be good to enable this too. I'd check both with this setting on and off, as some devices can cause problems with this setting on. | ||
| + | Do NOT forward port 1701 (L2TP), this allows direct access to the L2TP server, bypassing IPSEC entirely and sending all your data unencrypted. The whole idea is that the IPSEC connection encrypts your data from end to end, and on the server end, this data will be passed on to port 1701 internally. | ||
=Old/custom VPN= | =Old/custom VPN= | ||
Revision as of 12:07, 10 February 2012
| Version | Status | Date Updated | Updated By |
|---|---|---|---|
| 710 | Unknown | N/A | N/A |
| 810 | Unknown | N/A | N/A |
| 1004 | Unknown | N/A | N/A |
| 1204 | Unknown | N/A | N/A |
| 1404 | Unknown | N/A | N/A |
| Usage Information | |||
VPN (Virtual Private Networking) provides secure communication to your core when you are away. It also offers a lot of potential for connecting multiple cores (between houses, apartments, etc.). This would enable families and friends to share security cameras, call/intercom each other for free via Asterisk, pipe security notifications to every device at every connected residence, and possibly even share media (legality?)
Contents
VPN in LinuxMCE 1004
In LinuxMCE 1004 there is an integrated L2TP server.
Setup
In the web admin -> Advanced -> Network settings, enable the "L2TP/IPSEC VPN server enabled" checkbox. You also need to fill in the pre-shared key and the IP range the VPN clients should use. Save the settings.
In Wizard -> Basic Info -> Users, check the "Can connect via VPN" for every user that should be able to connect via VPN. Click "Change VPN Password" for the user and enter a password for your VPN connection.
Connection
Different devices have different GUIs for setting up a VPN, so this is just a general description. To find specific description for your device, do a google search, we don't need descriptions for every possible device added to this article(Thank you!). Enter your host name, pre-shared key and give the connection a name. The L2TP secret is not used and should be left disabled. Enter your username(case sensitive) and your VPN password.
Notes
If you have another router or ADSL modem or something between the core and the internet, you need to check these settings: You need to forward UDP ports 500(IPSEC-IKE) and 4500(IPSEC-ESP-NAT) to the core. If your device can forward protocol 50/ESP, forward this too to the core. You don't need both 4500 and the ESP protocol at the same time, find out what works for you, and disable the other one. If the device has a IPSEC passthrough, it might be good to enable this too. I'd check both with this setting on and off, as some devices can cause problems with this setting on. Do NOT forward port 1701 (L2TP), this allows direct access to the L2TP server, bypassing IPSEC entirely and sending all your data unencrypted. The whole idea is that the IPSEC connection encrypts your data from end to end, and on the server end, this data will be passed on to port 1701 internally.
Old/custom VPN
The following is a hack to add VPN support to LinuxMCE for version prior to 1004. It may not even work anymore, and I would not recommend it.
Installing PPTP and OpenVPN on the core
Download the patches and vpn package
Apply the diff patch
cd /var/www/lmce-admin ; sudo patch -p0 < /tmp/vpn.svn.diff
Install the php scripts
cd /var/www/lmce-admin ; sudo tar -xvf /tmp/vpn-php.tar
Install the package
sudo dpkg -i /tmp/lmce-vpn-scripts_1-2_all.deb
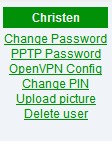
Now go to the web admin -> users and check out your new links.
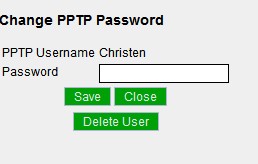
Click the PPTP Password link to set up PPTP and set user passwords. Click "Delete User" to disable PPTP for that user only.
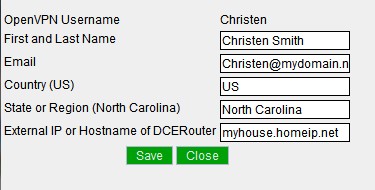
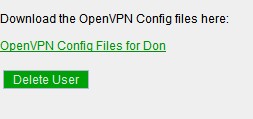
Click OpenVPN Config to set up OpenVPN and generate user configurations
Once the set up is finished, you can download the configs or Delete the user.
Setting up the VPN clients
Requirements for a VPN plugin
- Security
- Encryption
- Secure method of "pairing" houses
This could be done by sharing a public key with whomever you wish to pair with. User 1 would enter User 2's public key along with an optional message. User 2 would manually approve User 1 for pairing, and the cores would connect securly via VPN and automatically share security notifications and anything else set in a settings panel.
- Options panel for data to share with "paired" cores
Wish List
Add what you would like VPN to make possible in LinuxMCE